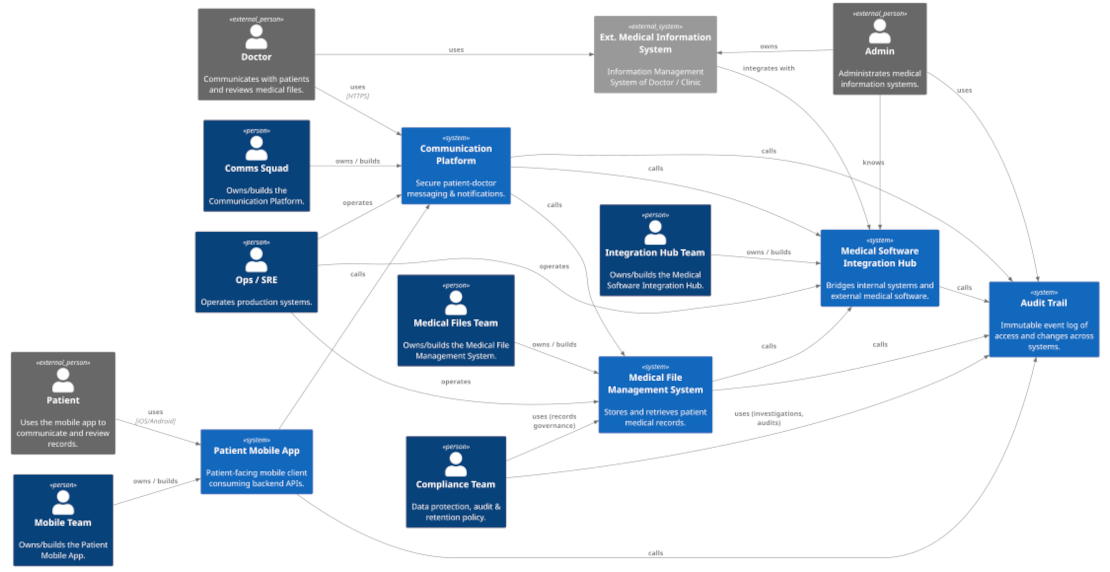
The 9 Talents in Software Teams
Job titles like “Senior Engineer” or “Principal Engineer” don’t explain how someone actually contributes to a team. Counting a candidate’s years of experience doesn’t tell you whether they’ll bring stability in a crisis, explore new ideas, or quietly hold a group together when things get messy.
After leading different engineering teams and organizations, I’ve seen the same profiles appear again and again, regardless of title or tech stack. These profiles shape how teams perform, where they get stuck, and how they grow. Over time, I began to think of them as archetypes of engineering talent: Patterns of behavior and impact that show up in every healthy software team.
Read More